Seed Phrases: A Single Point of Failure
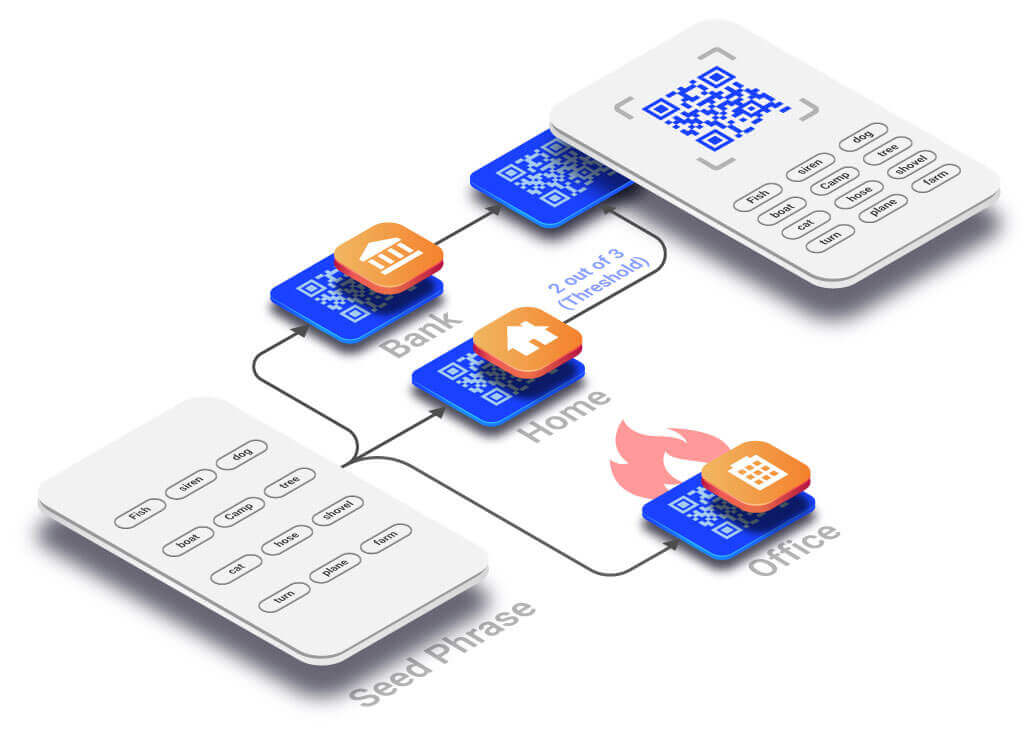
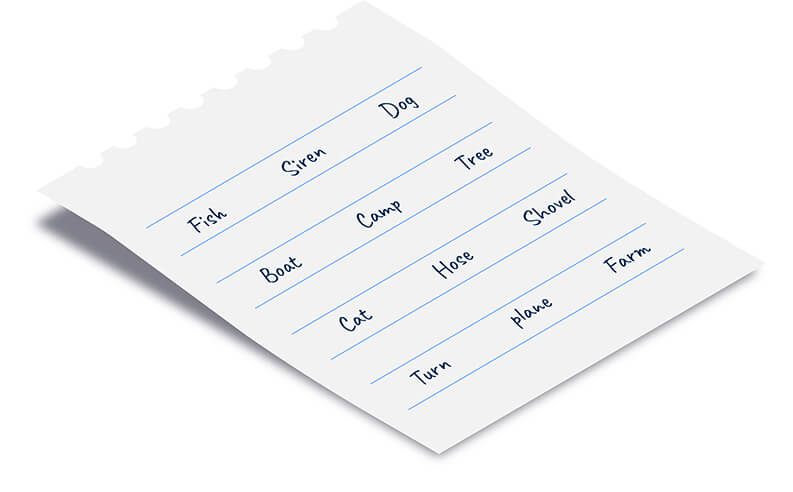
To maintain control over digital assets and safeguard them against online hackers, assets should be stored in self-custody wallets. These wallets provide seed phrases that must be stored securely and offline. Unfortunately, seed phrases are “a single point of failure” because they are stored in plain text format. This single copy, plain text format, exposes the owner to total asset loss through theft, damage, or loss of the seed phrases. The susceptibility to theft increases when the owner makes multiple copies to protect against damage or loss.
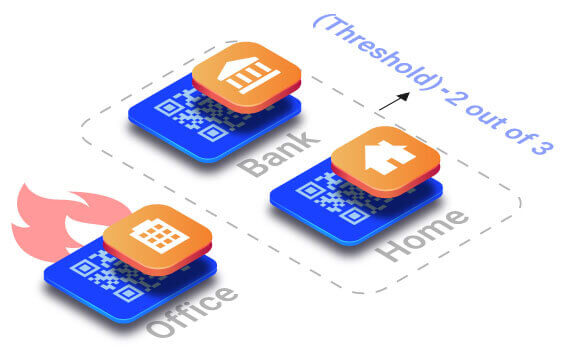
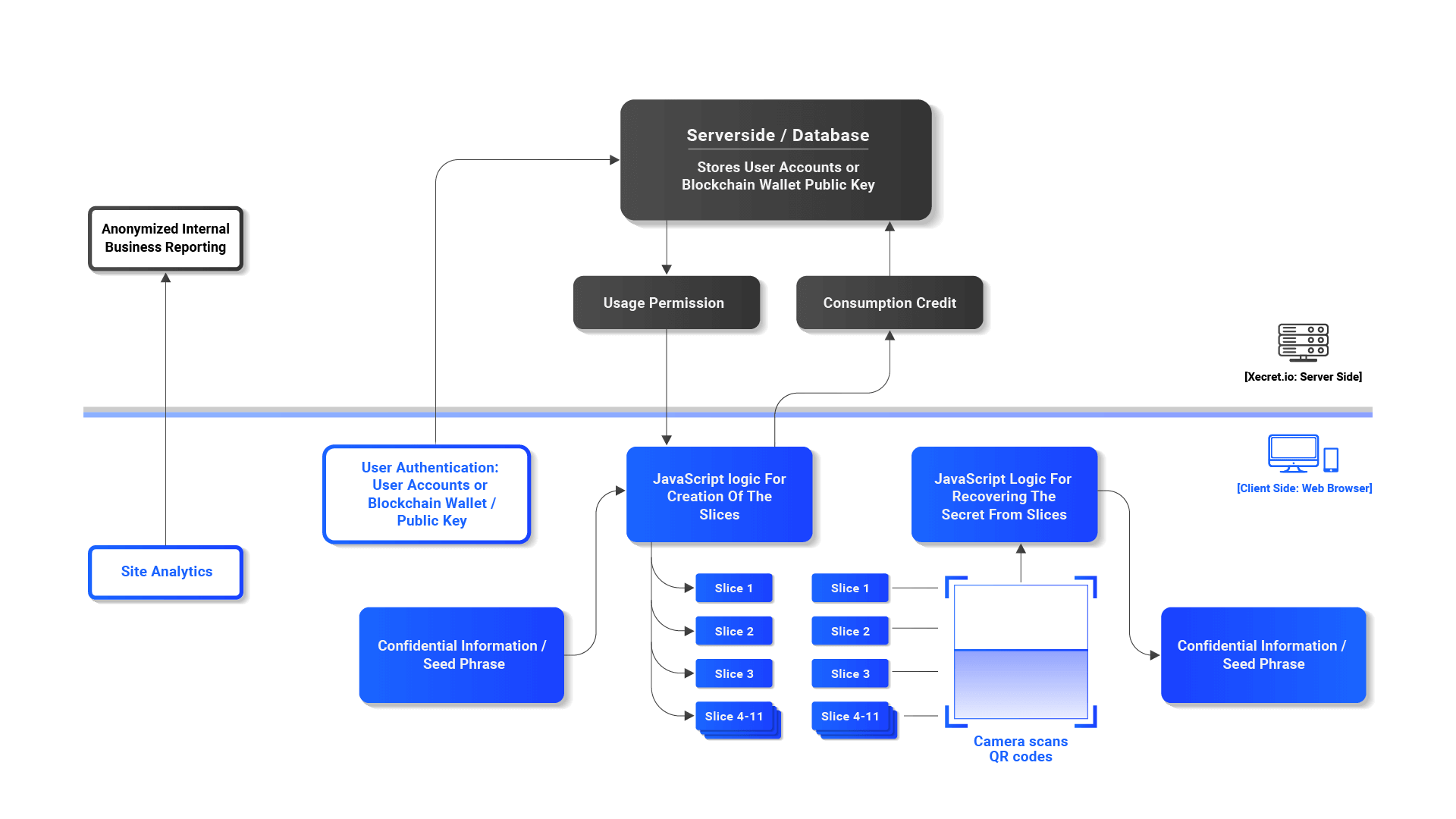
Xecret.io runs the seed phrase through a proprietary information dispersal algorithm (IDA) to create multiple data slices in the form of printable cryptographic QR codes. read more... Once QR codes are physically separated, the owner’s seed phrases are secure. Seed phrases are not recoverable from a single QR code because the IDA requires two or more QR codes to meet the minimum threshold for recovering the seed phrase. By incorporating the Xecret.io solution, the seed phrase ceases to be a point of failure.